With the announcement of the European Digital Identity (EUDI), digital wallets appear to be the moral winner in the debate over which solution is best for taking more control over one’s data. But is this a valid conclusion? In this blog post, we introduce you into the world of digital wallets, data safes and key safes.
What are wallets, data safes and key safes?
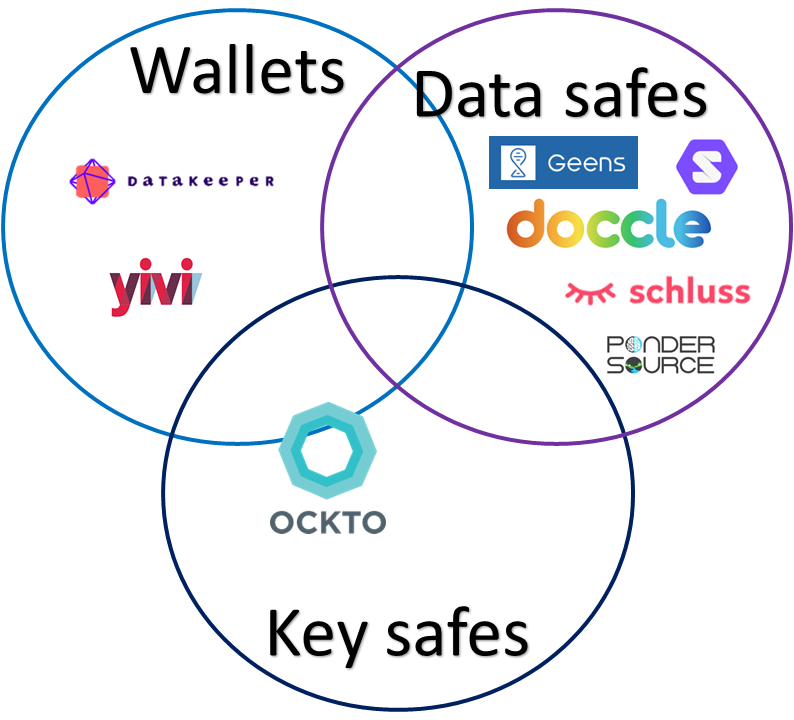
Wallets, data safes and key safes share the same goal: to give the individual user more control over their personal data. However, these solutions provide different implementations of this goal in practice. To better understand whether these solutions compete or complement each other, it is important to understand how they work. The absence of formal definitions often leads to confusion in discussions, so below we offer a brief explanation of each concept.
Wallets
Wallets are mobile apps that allow you to collect, store and share verifiable proofs (in the form of Verifiable Credentials) from your smartphone. Wallets are the digital counterparts of your physical wallet, containing various cards that convey information about you and can be used to prove aspects of your identity, such as your age. The credentials collected in your wallet are structured data, such as date of birth, name or diploma. It easily allows for data minimisation for example by only indicating that a person is older than 18 years instead of showing the full date of birth. Examples of Dutch wallets include YiVi (formerly IRMA) and DataKeeper.
Data Safes
Data safes are (decentralised) cloud solutions which can store various data. These could be considered as privacy and security-friendly alternatives to Dropbox and Google Drive with elaborated functionality for data management and sharing. Solid Pods are a well-known example, but companies like Doccle and Geens also offer these solutions as part of their services. Data safes allow the storage of both structured and unstructured data, enabling the collection of credentials as well as documents or health data (e.g., from a fitness tracker). Data safes often provide granular access and authorisation management, making it easier for new service providers to offer competitive services based on data stored in your digital data safe.
Digital key safes
Editorial note: In the original Dutch blog post, we used “sluis” (lock/sluice) instead of key safe, but sluis and lock have a different association. Sluis is closely associated with making water flow in the right direction (or data in this case).
Digital key safes differ from wallets and data safes in a crucial aspect: they do not store the user’s data (or do so only as briefly as possible). Instead, they enable individuals to give permission and share their data directly between data sources and service providers. Key safes should not be confused with password safes/managers, which have a slightly different goal. With key safes, users do not have to manage copies of their own data. Consent management plays an explicit role in data sharing processes in these solutions. Consent for data sharing can be either one-time or long-term. A Dutch example like the digital key safe model is the Ockto Brondata service, where users gather their data to share directly with the service provider, such as a mortgage lender.
The differences between wallets, data safes, and key safes
To better understand wallets, data safes, and key safes, it is necessary to understand the differences between these solutions. The MyData Operator reference model is an internationally validated model for understanding and comparing various Personal Data Management (PDM) solutions (wallets, data safes, and key safes).
The MyData operator reference model explained
(Source: MyData Operator white paper)
The set of functional elements that a MyData Operator implements influences the functionalities that an operator can offer to the individuals and other entities in the ecosystem. Each of the nine core functional elements enables some unique capability that is not covered by any other element. However, the elements should not be considered in isolation as most of the functionalities that are valuable to the other parties in the ecosystem involve more than one functional element. …
- Identity management (IM) functional element enables the identification and authentication of the different actors involved in data exchange.
- Permission management (PM) functional element enables the configuration and authorisation of data exchanges that are allowed to happen (e.g. notices, consents, permissions, mandates, legal bases, purposes, and preferences), and collection and handling of such authorisations.
- Service management (SM) functional element enables maintenance of a register of known actors and information about them (e.g. supported data models, preferences, and discovery information) in the data ecosystem.
- Value exchange (VE) functional element enables accounting and the transfer of value (monetary or other forms of credits or reputation) related to the exchange of data.
- Data model management (DMM) functional element enables data harmonisation and conversion into specified formats, communicating semantics (meaning) of data with other ecosystem participants and interpreting standard data models to individuals.
- Personal data transfer (PDT) functional element enables data exchange between the ecosystem participants in a standardised and secure manner by implementing permissioned interfaces (e.g. APIs).
- Personal data storage (PDS) functional element enables data integration from multiple sources (including data created by a person) in personal data storage under the individuals’ control and serving data from PDS to data using services.
- Governance support (GS) functional element enables compliance with the underlying governance frameworks to establish trustworthy relationships between individuals and organisations.
- Logging and accountability (LA) functional element enables the maintenance of records (including record deletion) on data exchanges taking place and creating transparency about who accessed what and when and based on what permissions.
Using this reference model, clear differences regarding some of the elements emerge. These are explained below for each respective functional element:
Identity management
- Digital identity is a core functionality of the PDM solution, and the rest of the services build on it (wallets, data safes).
- Identity management supports the rest of the services, providing access to data sources. The digital identity may be used by the data source or service provider (wallets, data safes, key safes).
Permission management
- Permission management is always essential in PDM solutions, but there is a significant difference in how explicit consent must be given (and therefore the level of experienced ‘friction’ in the UX).
Data model management
- Credential-based: Contains structured data in the form of credentials, making it easily machine-readable (wallets, data safes, key safes).
- Unstructured and semi-structured data: Allows more diversity in data, including text documents. Processing unstructured data automatically is more challenging (data safes, key safes).
Personal data storage
- Completely decentralised data storage with only a local copy on a smartphone (wallets)
- Partially decentralised with a copy or original in a (decentralised) cloud solution (data safes)
- No data storage (digital key safes)
Personal data transfer
- Data is shared directly from the data source to the relying party (digital key safes). The data can pass through the PDM solution or go directly. In the latter case, the PDM solution only records the consent.
- Data is first issued and stored and then shared at a later point in time (wallets and data safes)
The above overview of differences and similarities helps when trying to determine which PDM solution is most suitable for a specific service. When comparing specific providers, it is also important to realise that there are significant differences in maturity, adoption, and business models of the solution.
Wallets, data safes and key safes complement each other
The wallet may seem like the moral winner due to the attention on the European Digital Identity, but this conclusion should not be drawn too quickly. Wallets, data safes, and key safes have important differences, each with its own advantages and disadvantages. In some cases, these different approaches may even complement each other. Consider having your medication prescriptions in the wallet that you always carry with you and an extensive health dossier in a data safe solution. The best solution depends heavily on the use case or service the user wants to engage with.
Do you want to learn more? Check out the “Understanding MyData Operators” whitepaper and reach out to Koen de Jong.
How Can I Find Out More and Participate?
- Join MyData Global as a member
- Join MyData Slack and discussions at the decentralised-identity channel
- Follow MyData Global LinkedIn and X feeds
- Subscribe to our newsletter
- Sign the MyData Declaration
This blog is authored by Koen de Jong, an expert in the fields of Digital Identities and Personal Data Management. He is working at InnoValor Advies, a MyData Global founding member, and an active member within the MyData community. For the last three years, Koen has led the Operator thematic group and been one of the review team members for the MyData Awards. Currently, he is involved with setting up the Dutch ecosystem for the European Digital Identity.
This post was originally published on the website of InnoValor Advies in Dutch. This is also why all mentioned operators are either from the Netherlands or Belgium.

